Example flow for services with service account mapping
The following diagram identifies the flow of authentication and authorization information for services with service account mapping. Colors are used in the following ways:
- Orange - credentials information
- Blue - endpoint access information
- Green - resource access information
- Red - proxy user and session user information
Some values are used to determine multiple types of access. These values initially appear as black (when they do not apply to a single type of access), and then later appear in one or more specific colors (to reflect the value is being used at that point in the process for a specific type of access).
In the following example, an API call is triggered by the Acme billing application, BillingApp.
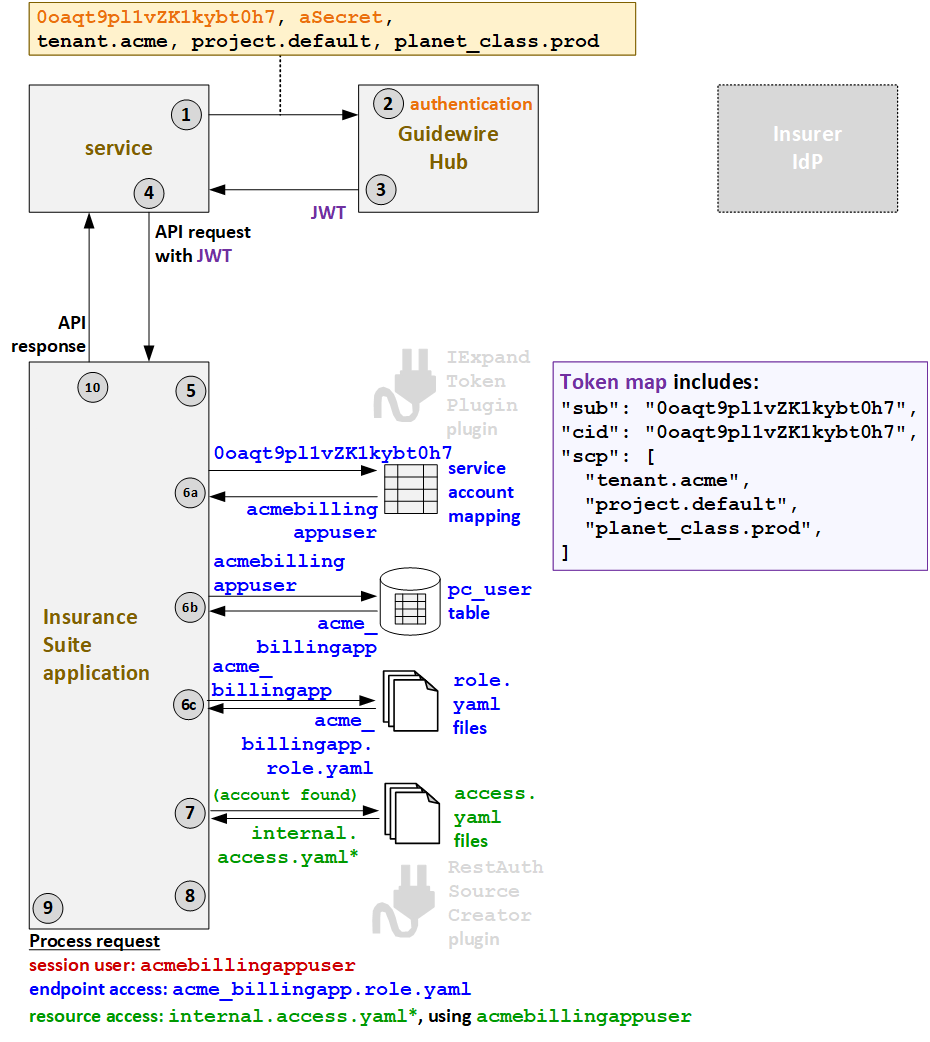
- When FNOLReporter triggers an API call, it must first request a JWT from Guidewire Hub.
The request for the JWT includes the client ID (
0oaqt9pl1vZK1kybt0h7), the secret (aSecret), and additional deployment information (tenant.acme,project.default,planet_class.prod). - Guidewire Hub authenticates the services based on the client ID and secret.
- Guidewire Hub generates a JWT and sends it to the service. This JWT includes the client
ID (
cid) and additional deployment information. - The service sends the API request to PolicyCenter along with the JWT.
- The IExpandTokenPlugin plugin is not relevant for services with service account mapping.
- PolicyCenter determines the endpoint access.
- First, PolicyCenter executes a lookup to map the client
ID (
0oaqt9pl1vZK1kybt0h7) to a service account name (acmebillingappuser). - Then, PolicyCenter queries for the user roles that this
account name has. One role is returned:
acme_billingapp. - Based on the returned role, the
acme_billingapp.role.yamlAPI role file is used to define the endpoint access.
- First, PolicyCenter executes a lookup to map the client
ID (
- Next, PolicyCenter determines the resource access
strategy. Based on the fact that the service account lookup found a valid service account,
PolicyCenter grants resource access as defined in the
internalaccess.yamlfiles. (* PolicyCenter starts withinternal_ext-1.0.access.yaml, but this file references additionalaccess.yamlfiles whose name starts with "internal".) - Proxy user access is not relevant for services with service account mapping.
- PolicyCenter processes the request.
- The session user is the service account:
acmebillingappuser. - The endpoint access is defined by
acme_billingapp.role.yaml. - The resource access is defined by
internalaccess.yamlusing the resource access ID ofacmebillingappuser.
- The session user is the service account:
- PolicyCenter provides the response to the initial call.