Example flow for basic authentication
The following diagram identifies the flow of authentication and authorization information for basic authentication. Colors are used in the following ways:
- Orange - credentials information
- Blue - endpoint access information
- Green - resource access information
- Red - proxy user and session user information
Sometimes, a value is used in different parts of the flow to determine different types of access. These values appear in the flow diagrams multiple times, but the color is changed to reflect how the value is being used at that point in the process.
In the following example, an API call is triggered by Alice Applegate, who is an internal user, using a browser-based application and basic authentication.
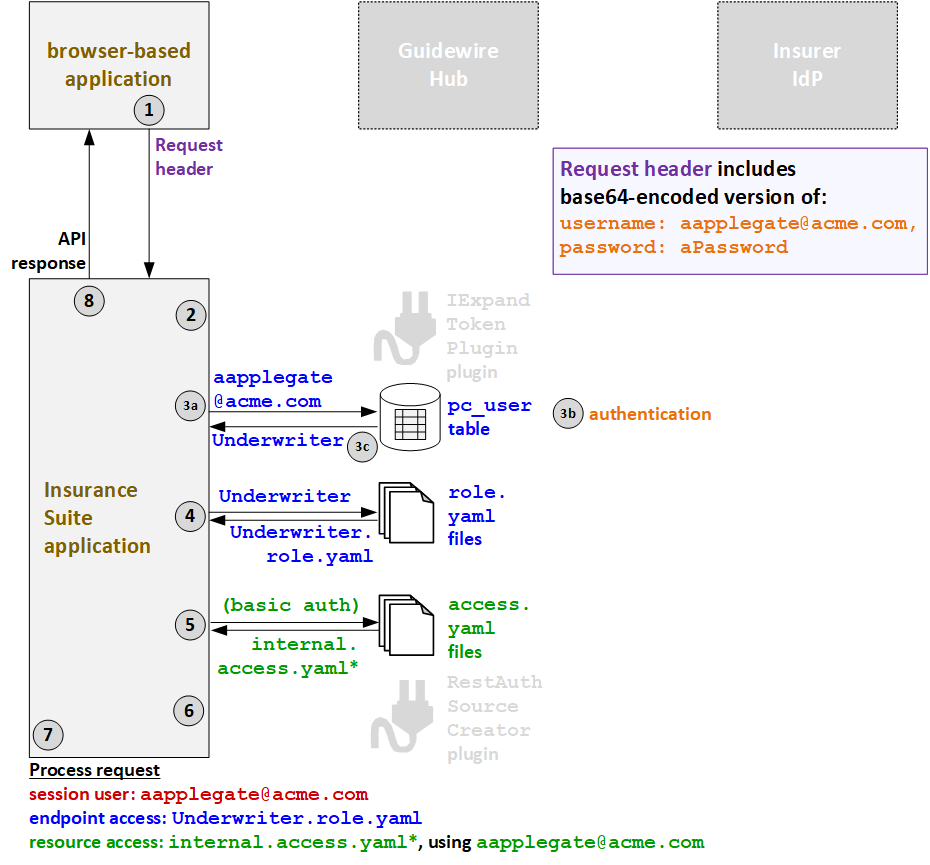
- When Alice triggers an API call, the caller application sends the API request to
PolicyCenter. The request header includes a base64-encoded
version of the user's user name (
aapplegate@acme.com) and password (aPassword). - The IExpandTokenPlugin plugin is not relevant for basic authentication.
- PolicyCenter authenticates the user and determines the
endpoint access.
- Using the user name in the request header (
aapplegate@acme.com), PolicyCenter queries the user table. - PolicyCenter authenticates the user by verifying that the user name and password match.
- PolicyCenter responds with the user roles that this user
has. One role is returned:
Underwriter.
- Using the user name in the request header (
- Based on the returned role, the
Underwriter.role.yamlAPI role file is used to define the endpoint access. - Next, PolicyCenter determines the resource access
strategy. Because the call is using basic authentication, PolicyCenter grants resource access as defined in the
internalaccess.yamlfiles. (* PolicyCenter starts withinternal_ext-1.0.access.yaml, but this file references additionalaccess.yamlfiles whose name starts with "internal".) - Proxy user access is not relevant for basic authentication.
- PolicyCenter processes the request.
- The session user is the internal user:
aapplegate@acme.com. - The endpoint access is defined by
Underwriter.role.yaml. - The resource access is defined by
internalaccess.yamlusing the resource access ID ofaapplegate@acme.com.
- The session user is the internal user:
- PolicyCenter provides the response to the initial call.