Example flow for services with user context
The following diagram identifies the flow of authentication and authorization information for services with user context. Colors are used in the following ways:
- Orange - credentials information
- Blue - endpoint access information
- Green - resource access information
- Red - proxy user and session user information
Some values are used to determine multiple types of access. These values initially appear as black (when they do not apply to a single type of access), and then later appear in one or more specific colors (to reflect the value is being used at that point in the process for a specific type of access).
Services with user context: internal users
In the following example, an API call is triggered by the Acme policy billing application, BillingApp, on behalf of Alice Applegate, who is an internal user.
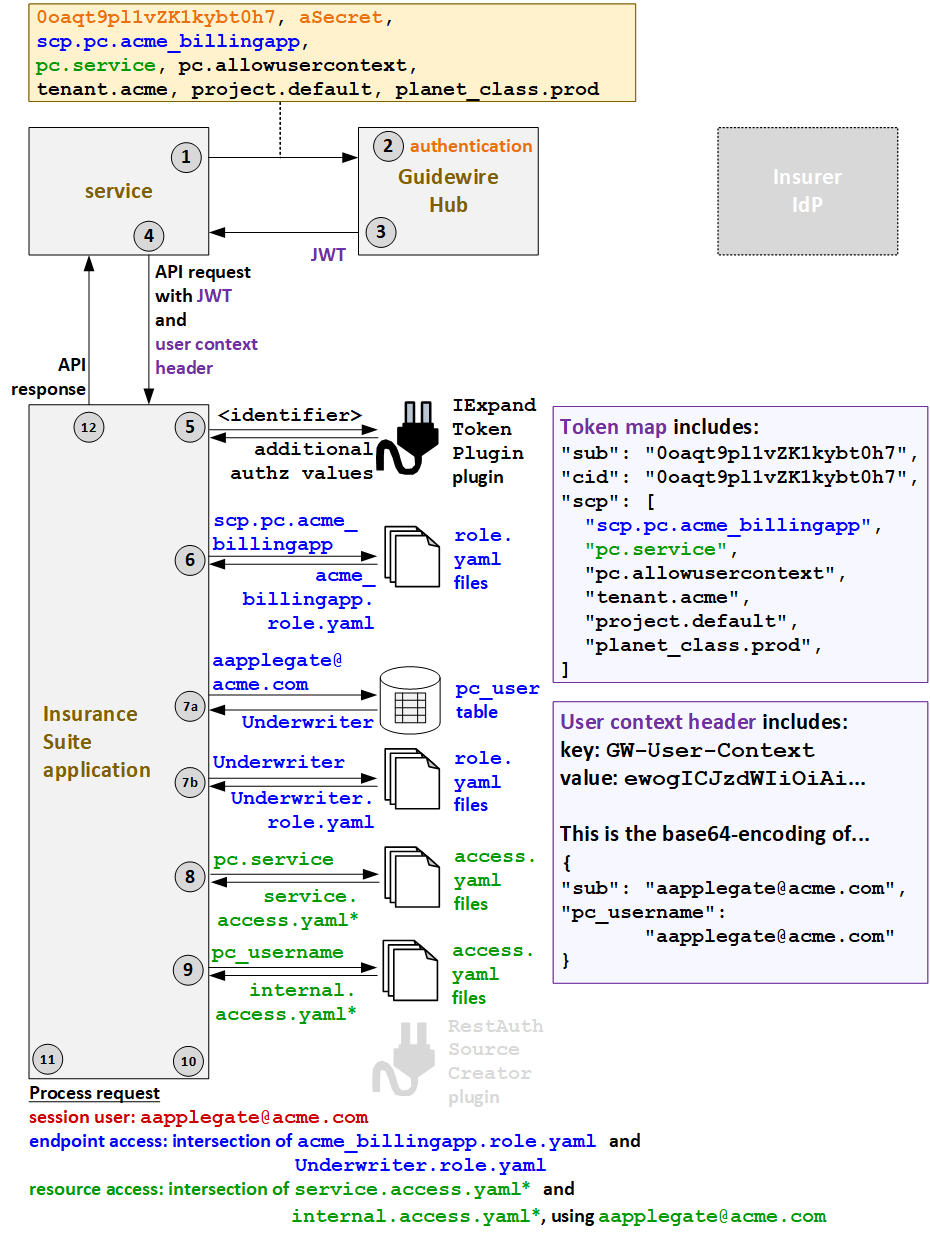
- When BillingApp triggers an API call, it must first request a JWT from Guidewire Hub.
The request for the JWT includes the client ID (
0oaqt9pl1vZK1kybt0h7), the secret (aSecret), the application's API role (scp.pc.acme_billingapp), the application's resource access strategy (pc.service), the fact that the call will be made for a user (pc.allowusercontext) and additional deployment information (tenant.acme,project.default,planet_class.prod). - Guidewire Hub authenticates the services based on the client ID and secret. It also verifies that the API role and resource access strategy provided in the request match what was specified when the service was registered with Guidewire Hub.
- Guidewire Hub generates a JWT and sends it to the service. This JWT includes the client
ID (
cid) and ascptoken claim which names the API role (scp.pc.acme_billingapp), the resource access strategy (pc.service), thepc.allowusercontextvalue (which indicates that user information is specified in an additional user context header), and additional deployment information. - The service sends the API request to PolicyCenter along
with the JWT and a user context header that identifies the user
(
aapplegate@acme.com), the user's resource access strategy (pc_username), and resource access ID (aapplegate@acme.com). - PolicyCenter extracts the information in the JWT into a
token map. Then, the IExpandTokenPlugin plugin calls any relevant authorization
applications to retrieve any relevant additional auth values that must be added to or
modified in the token map. (The IExpandTokenPlugin plugin can affect only the information
that normally comes in the JWT. It cannot affect information in a user context header.
Therefore, for services with user context, an insurer could choose to retrieve either the
service's API role (such as
scp.pc.acme_billingapp) or the service's resource access strategy name (pc.service) using the IExpandTokenPlugin plugin. But the API roles and resource access IDs for the user must be in the user context header when the call is sent to PolicyCenter.) - PolicyCenter must determine the endpoint access at both
the service level and the user level. It starts at the service level. Based on the API
role value in the JWT (
scp.pc.acme_billingapp), theacme_billingapp.role.yamlAPI role file is used to define the service-level access. - Next, PolicyCenter determines the user-level endpoint
access.
- Using the user name in the user context header
(
aapplegate@acme.com), PolicyCenter queries for the user roles that this user has. One role is returned:Underwriter. - Based on the returned role, the
Underwriter.role.yamlAPI role file is used to define the user-level access.
- Using the user name in the user context header
(
- PolicyCenter must also determine the resource access at
the service level and the user level. It starts with the service-level resource access
strategy. Based on the resource access strategy value in the JWT
(
pc.service), it grants service-level resource access as defined in theserviceaccess.yamlfiles. (* PolicyCenter starts withservice_ext-1.0.access.yaml, but this file references additionalaccess.yamlfiles whose name starts with "service".) - PolicyCenter determines the user-level resource access
strategy. Based on the resource access strategy value in the user context header
(
pc_username), it grants user-level resource access as defined in theinternalaccess.yamlfiles. (* PolicyCenter starts withinternal_ext-1.0.access.yaml, but this file references additionalaccess.yamlfiles whose name starts with "internal".) - Proxy user access is not relevant for services with user context when the user is an internal user.
- PolicyCenter processes the request.
- The session user is the internal user:
aapplegate@acme.com. - The endpoint access is the intersection of the endpoints and operations defined
granted at the service level (
acme_billingapp.role.yaml) and at the user level (Underwriter.role.yaml). Endpoints, operations, and fields must be listed at both levels to be available to the call. - The resource access is the intersection of the resources accessible to the service (as
defined in the
serviceaccess.yaml) and the resources available to the user (as defined in theinternalaccess.yamlusing the resource access ID ofaapplegate@acme.com). In the base configuration, theserviceaccess.yamlfiles make all resources available. Therefore, logically speaking, the service-level resource access does not specify any restrictions. The call can access any resource provided it is available through the user-level resource access.
- The session user is the internal user:
- PolicyCenter provides the response to the initial call.
Services with user context: external users
In the following example, an API call is triggered by the Acme policy billing application, BillingApp, on behalf of Ray Newton, who is an external user.
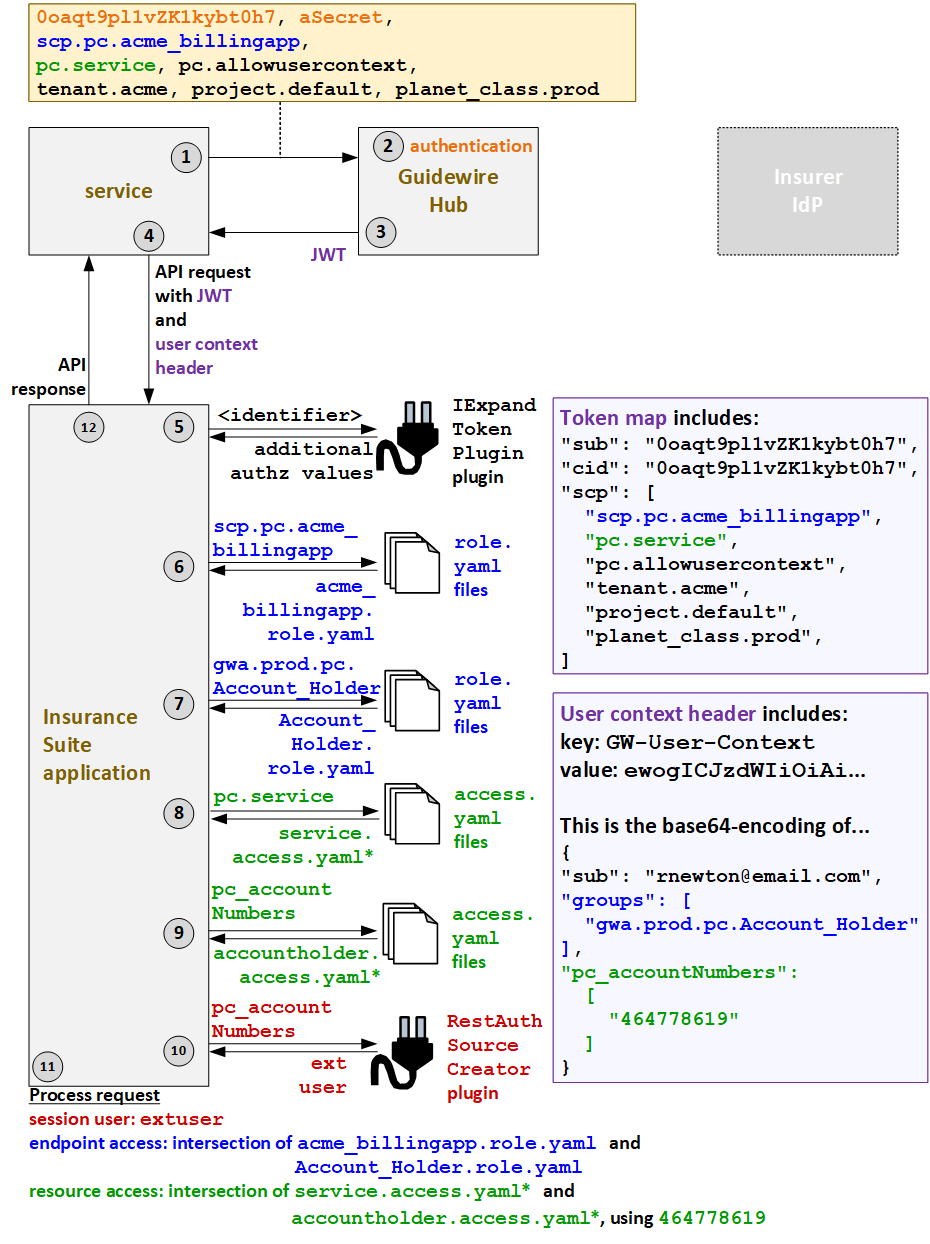
- When BillingApp triggers an API call, it must first request a JWT from Guidewire Hub.
The request for the JWT includes the client ID (
0oaqt9pl1vZK1kybt0h7), the secret (aSecret), the application's API role (scp.pc.acme_billingapp), the application's resource access strategy (pc.service), the fact that the call will be made for a user (pc.allowusercontext) and additional deployment information (tenant.acme,project.default,planet_class.prod). - Guidewire Hub authenticate the services based on the client ID and secret. It also verifies that the API role and resource access strategy provided in the request match what was specified when the service was registered with Guidewire Hub.
- Guidewire Hub generates a JWT and sends it to the service. This JWT includes the client
ID (
cid) and ascptoken claim which names the API role (scp.pc.acme_billingapp), the resource access strategy (pc.service), thepc.allowusercontextvalue (which indicates that user information is specified in an additional user context header), and additional deployment information. - The service sends the API request to PolicyCenter along
with the JWT and a user context header that identifies the user
(
rnewton@email.com), the user's resource access strategy (pc_accountNumbers), and resource access ID (464778619). - PolicyCenter extracts the information in the JWT into a
token map. Then, the IExpandTokenPlugin plugin calls any relevant authorization
applications to retrieve any relevant additional auth values that must be added to or
modified in the token map. (The IExpandTokenPlugin plugin can affect only the information
that normally comes in the JWT. It cannot affect information in a user context header.
Therefore, for services with user context, an insurer could choose to retrieve either the
service's API role (such as
scp.pc.acme_billingapp) or the service's resource access strategy name (pc.service) using the IExpandTokenPlugin plugin. But the API roles and resource access IDs for the user must be in the user context header when the call is sent to PolicyCenter.) - PolicyCenter must determine the endpoint access at both
the service level and the user level. It starts at the service level. Based on the API
role value in the JWT (
scp.pc.acme_billingapp), theacme_billingapp.role.yamlAPI role file is used to define the service-level access. - Next, PolicyCenter determines the user-level endpoint
access. Based on the contents of the
groupstoken claim in the user context header (gwa.prod.pc.Account_Holder), theAccount_Holder.role.yamlAPI role file is used to define the user-level access. - PolicyCenter must also determine the resource access at
the service level and the user level. It starts with the service-level resource access
strategy. Based on the resource access strategy value in the JWT
(
pc.service), PolicyCenter grants service-level resource access as defined in theserviceaccess.yamlfiles. (* PolicyCenter starts with service_ext-1.0.access.yaml, but this file references additionalaccess.yamlfiles whose name starts with "service".) - Next, PolicyCenter determines the user-level resource
access strategy. Based on the resource access strategy value in the user context header
(
pc_accountholder), it grants user-level resource access as defined in theaccountholderaccess.yamlfiles. (* PolicyCenter starts withaccountholder_ext-1.0.access.yaml, but this file references additionalaccess.yamlfiles whose name starts with "accountholder".) - To determine which proxy user to assign to the session, PolicyCenter calls the
RestAuthenticationSourceCreatorplugin. The user context header specified a resource access strategy ofpc_accountNumbers. So, the plugin returns the proxy user for external users:extuser. - PolicyCenter processes the request.
- The session user is the proxy external user:
extuser. - The endpoint access is the intersection of the endpoints and operations defined
granted at the service level (
acme_billingapp.role.yaml) and at the user level (Account_Holder.role.yaml). Endpoints, operations, and fields must be listed at both levels to be available to the call. - The resource access is the intersection of the resources accessible to the service
(as defined in the
serviceaccess.yaml) and the resources available to the user (as defined in theaccountNumbersaccess.yamlusing the resource access ID of464778619). In the base configuration, theserviceaccess.yamlfiles make all resources available. Therefore, logically speaking, the service-level resource access does not specify any restrictions. The call can access any resource provided it is available through the user-level resource access.
- The session user is the proxy external user:
- PolicyCenter provides the response to the initial call.