Example flow for internal users
The following diagram identifies the flow of authentication and authorization information for internal users. Colors are used in the following ways:
- Orange - credentials information
- Blue - endpoint access information
- Green - resource access information
- Red - proxy user and session user information
Some values are used to determine multiple types of access. These values initially appear as black (when they do not apply to a single type of access), and then later appear in one or more specific colors (to reflect the value is being used at that point in the process for a specific type of access).
In the following example, an API call is triggered by Alice Applegate, who is an internal user, using a browser-based application.
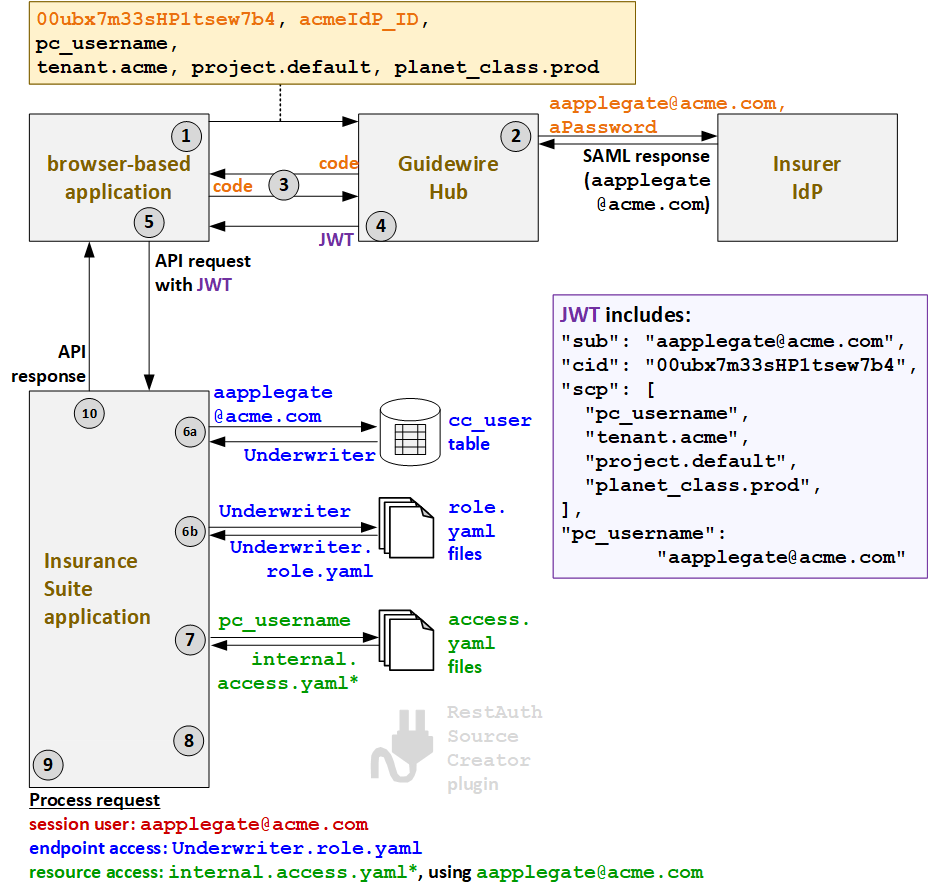
- When Alice triggers an API call, the caller application must first request a JWT from
Guidewire Hub. To initiate the process of getting the JWT, the caller application submits
its client ID (
00ubx7m33sHP1tsew7b4), the ID of the IdP (acmeIdP_ID), the application's resource access strategy (pc.username), and additional deployment information (tenant.acme,project.default,planet_class.prod). - To authenticate the user, Guidewire Hub acquires the user's user name
(
aapplegate@acme.com) and password (aPassword) through some type of login screen. It sends this information to the appropriate IdP. The IdP authenticates the user and provides a SAML response with the user's name (aapplegate@acme.com). - Guidewire Hub sends a code to the caller application. The caller application uses this code to request a JWT.
- Guidewire Hub generates a JWT and sends it to the caller application. This JWT includes
the client ID (
cid), ascptoken claim which names the resource access strategy (pc_username) and additional deployment information, and apc_usernametoken which names the user's resource access ID (aapplegate@acme.com). - The caller application sends the API request to PolicyCenter along with the JWT.
- PolicyCenter determines the endpoint access.
- Using the user name in the JWT (
aapplegate@acme.com), PolicyCenter queries for the user roles that this user has. One role is returned:Underwriter. - Based on the returned role, the
Underwriter.role.yamlAPI role file is used to define the endpoint access.
- Using the user name in the JWT (
- Next, PolicyCenter determines the resource access
strategy. Based on the resource access strategy value in the JWT
(
pc_username), it grants resource access as defined in theinternalaccess.yamlfiles. (* PolicyCenter starts withinternal_ext-1.0.access.yaml, but this file references additionalaccess.yamlfiles whose name starts with "internal".) - Proxy user access is not relevant for internal users.
- PolicyCenter processes the request.
- The session user is the internal user:
aapplegate@acme.com. - The endpoint access is defined by
Underwriter.role.yaml. - The resource access is defined by
internalaccess.yamlusing the resource access ID ofaapplegate@acme.com.
- The session user is the internal user:
- PolicyCenter provides the response to the initial call.