Hardening Guidance for InsuranceSuite
As Guidewire's customers accelerate their journey to the cloud, ensuring they can operate securely and with confidence is a top priority. Your success in the cloud depends on a clear understanding of the shared responsibility model and the specific actions you can take to protect your environments.
To that end, this guide provides a single, authoritative framework of recommended security controls for Guidewire InsuranceSuite. The result of a collaborative effort across Guidewire's security, product, and services organizations, its purpose is to empower customers to protect their data, reduce their attack surface, and build a security posture that is resilient, compliant, and ready for the future.
Why Security Hardening is Essential
InsuranceSuite is a mission-critical cloud platform that processes and stores vast amounts of sensitive data. While Guidewire provisions a secure cloud foundation, the principle of shared responsibility means that you take ownership of application-level security.
Effective hardening is not just a best practice; it is an essential discipline that directly mitigates critical security risks stemming from customer-managed configurations, including:
- Misconfigured or overly permissive user roles.
- Over-privileged integration or service accounts.
- Lack of Multi-Factor Authentication (MFA) enforcement.
- Insecure or improperly exposed APIs.
- Weak data governance and access control policies.
- Reliance on vulnerable or outdated custom libraries.
- Inadvertent exposure of sensitive data (PII) through misconfigured settings.
By following this guide, you will strengthen your security posture by:
- Reducing the Attack Surface: Systematically limiting unnecessary features, access points, and integrations to minimize potential vulnerabilities.
- Strengthening Access Controls: Enforcing strong authentication and granular authorization to ensure only the right people have the right access.
- Layering Data Defenses: Protecting sensitive information with a multi-faceted approach that includes encryption, data masking, and strict access policies.
- Enabling Threat Visibility: Implementing robust logging and monitoring to detect, investigate, and respond to suspicious activities swiftly.
By following this hardening guide, administrators, cloud engineers, and security teams can strengthen the security posture of their InsuranceSuite deployments while ensuring compliance with industry standards.
Scope of This Guide
This guidance applies to customer-managed configurations within InsuranceSuite, including PolicyCenter, ClaimCenter, and BillingCenter, as well as their associated integrations in Guidewire SaaS deployments.
The focus is on hardening InsuranceSuite itself rather than AWS infrastructure security. It provides best practices for:
- Identity and Access Management (IAM) – Secure user access to InsuranceSuite.
- Data Security and Governance – Ensure sensitive customer data is encrypted and masked.
- Application and Development Security – Integrate security into the entire development lifecycle, from code and components to pipelines and production configurations.
- Logging and Monitoring – Capture security logs and integrate them with Security Information and Event Management (SIEM) solutions.
Audience
This document is intended for Security Administrators, IT Professionals, Guidewire Platform Owners, Compliance Officers, and other security and compliance stakeholders responsible for operationalizing platform security.
How to Use This Guide
This guide provides our expert advice on securing your Guidewire implementation. Under the Guidewire Cloud Shared Responsibility Model, while Guidewire secures the underlying platform, you are responsible for the secure configuration of your tenant. The following control objectives represent our opinionated, best-practice recommendations to help you effectively manage your side of this shared responsibility and reduce your overall risk.
Successful implementation of these controls is a collaborative effort. Work closely with your implementation team, security partners, and privacy office to ensure these objectives are incorporated into your go-live plan and continuously maintained post-deployment.
Exclusions
This guide does not cover AWS infrastructure security (IAM, VPC security, AWS Shield, etc.), as those are handled at the cloud hosting level.
Assumptions
Before implementing the recommendations in this guide, we assume that:
- InsuranceSuite is hosted on GWCP, and foundational AWS security controls are in place.
- AWS IAM, networking, and monitoring services are already configured per Guidewire’s best practices.
- Your implementation and security teams have the necessary internal resources and authority to implement the controls in this guide, including the ability to request platform changes through official Guidewire support channels.
Shared Responsibility Model
A clear understanding of the shared responsibility model is fundamental to securing InsuranceSuite. Responsibilities are divided as follows:
Guidewire is responsible for:
- Managing the security of the cloud infrastructure (IaaS/PaaS).
- Securing the underlying runtime environment and operating systems.
- Maintaining the baseline platform configuration and core application security.
- Implementing and managing encryption for data at rest and in transit within the platform.
- Applying security patches to the core application and underlying infrastructure.
- Conducting internal monitoring of the platform for security and availability.
- Securing the core network infrastructure, including VPCs, subnets, and network gateways.
The Customer is responsible for:
- Managing user identity, roles, and permissions (Role-Based Access Control).
- Enforce strong authentication, including Multi-Factor Authentication (MFA).
- Securing API authentication and managing integration account credentials.
- Defining security controls for custom integrations and extensions.
- Implementing data classification and governance policies for their data.
- Monitoring user activity and security logs provided by the platform.
- Ensuring the security of customer-specific configurations and code.
- Configuring secure connectivity services, such as mutual TLS (mTLS) for integrations and AWS PrivateLink for private network connections.
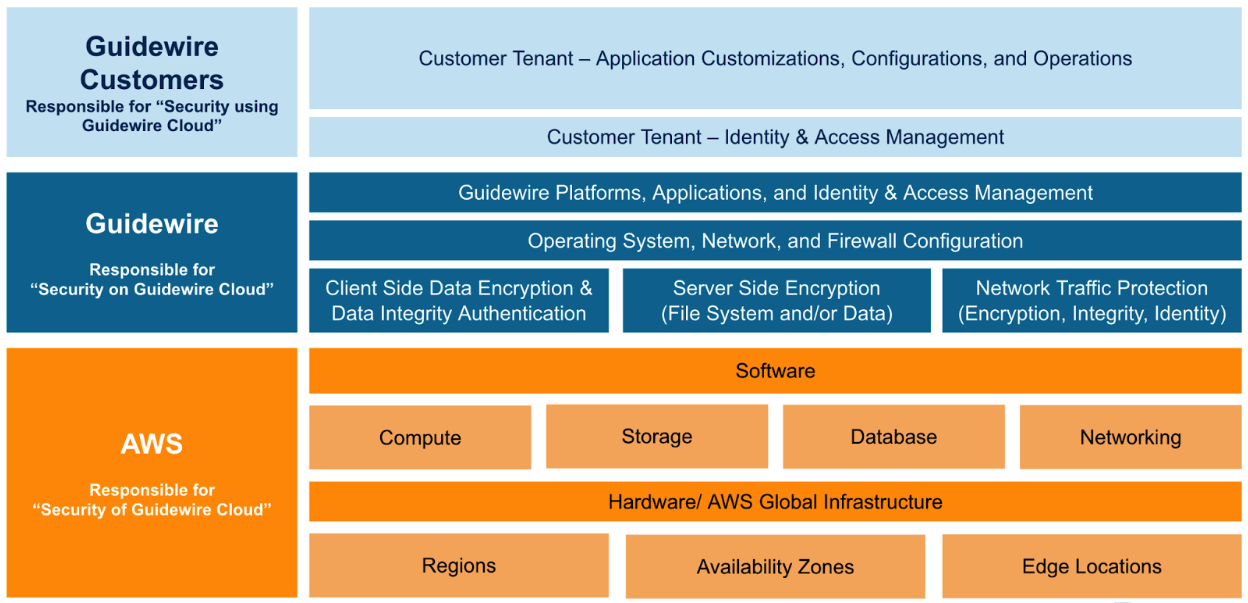 Shared Responsibility Model Reference for Guidewire
Shared Responsibility Model Reference for Guidewire
Overarching Principles
All security hardening efforts for InsuranceSuite are governed by these core principles
- Shared Responsibility Model: Guidewire secures the SaaS infrastructure and core application services; customers are responsible for user access, integrations, and secure configurations.
- Least Privilege: Limit access rights for users and services to the bare minimum necessary.
- Secure Network by Default: All network access should be restricted on a least-privilege basis. Exposing any application or port to the public internet (for example, allowing access from 0.0.0.0/0) is not a recommended practice unless it's explicitly required for a public-facing service and has undergone a formal risk assessment.
- Defense in Depth: Layer security across identity, data, application, and network levels.
- Continuous Monitoring and Improvement: Utilize provided audit trails and logs to review system activity regularly.
- Compliance Adherence: Maintain alignment with regulatory standards, including GDPR, HIPAA, SOC 2, and ISO 27001.
By applying the security hardening measures in this guide, teams can minimize security risks, protect customer data, and ensure compliance with regulatory requirements.
Resources
Guidewire Cloud Standards:
Guidewire Community:
Guidewire:
- Security administration
- Securing access to contact information
- Security: roles, permissions, and the community model
- Data encryption
AWS:
Was this page helpful?